With the rise of eCommerce and mobile payments, remote transactions where the physical card is not present – also known as card-not-present, or CNP, transactions – have become increasingly common. However, the lack of physical card verification makes these transactions more vulnerable to fraud.
In this comprehensive guide, we’ll explore what card-not-present transactions are, the different types, how they work, the parties involved, the fraud risks, and the best practices merchants should follow to accept CNP payments securely.
Whether operating an online storefront or accepting payments over the phone, understanding CNP transactions is crucial for mitigating fraud and providing a seamless customer experience.
What Is a Card-Not-Present Transaction?

A card-not-present transaction occurs when a payment is made without the physical presentation of the credit or debit card. This typically happens in online shopping, over-the-phone purchases, or any situation where the cardholder does not physically swipe, insert, or tap their card on a payment terminal.
In these transactions, the cardholder provides their card details via a website, phone, or another remote means. The essential information includes the card number, expiration date, a security code such as the CVV, and, in some cases, a ZIP code.
CNP transactions are inherently more prone to fraud than card-present transactions, where the card and cardholder are physically present at the point of sale. This increased risk is inherent to the situation because verifying the cardholder’s identity is more challenging without physical card inspection and using security features like PINs or chip technology.
As a result, businesses engaging in CNP transactions often implement additional security measures, such as address verification systems (AVS), two-factor authentication, or secure payment gateways to mitigate the risks of fraudulent activities.
What Are The Types of Card-Not-Present Transactions?
Here are the main types of CNP transactions, each with its unique characteristics:
Online transactions: The most common type of CNP transactions occur online as eCommerce transactions. Customers enter their credit or debit card information on a website or mobile app to make a purchase. This requires the card number, expiration date, and the CVV code. Online transactions often incorporate additional security measures like Secure Sockets Layer (SSL) encryption and may use payment gateways for enhanced security.
Phone orders: These transactions happen when a customer provides their card details over the phone to a merchant. This method is commonly used for food delivery, catalog purchases, or customer support-driven sales. Since there’s no physical card to swipe, merchants manually enter the card details into their payment system. The security risk is higher in phone orders due to the lack of visual verification of the card and the cardholder.
Mail orders: Similar to phone orders, mail order transactions involve customers sending their card details through postal mail. This method is less common but is still used by some consumers who prefer offline shopping or do not have internet access. Security concerns are significant here due to the potential interception of card details during transit.
Recurring payments or subscriptions: This type involves storing the cardholder’s information to process payments regularly. Common examples include subscription services, memberships, and utility payments. The initial setup of the recurring payment might require a CNP transaction, after which the details are stored for future billing cycles. Security measures for recurring payments often include tokenizing card data to reduce the risk of data breaches.
Invoice payments: Used primarily in B2B transactions, this method involves sending an invoice to customers, who then enter their payment details on a payment platform to complete the transaction. This is often managed through a secure online portal.
Mobile payments: Mobile payments have become a significant type of CNP transaction. Apps like digital wallets (Apple Pay and Google Pay) allow users to store their card information securely and make payments through their mobile devices, often using technologies like near-field communication (NFC) for contactless payments.
How Do Card-Not-Present Transactions Work?
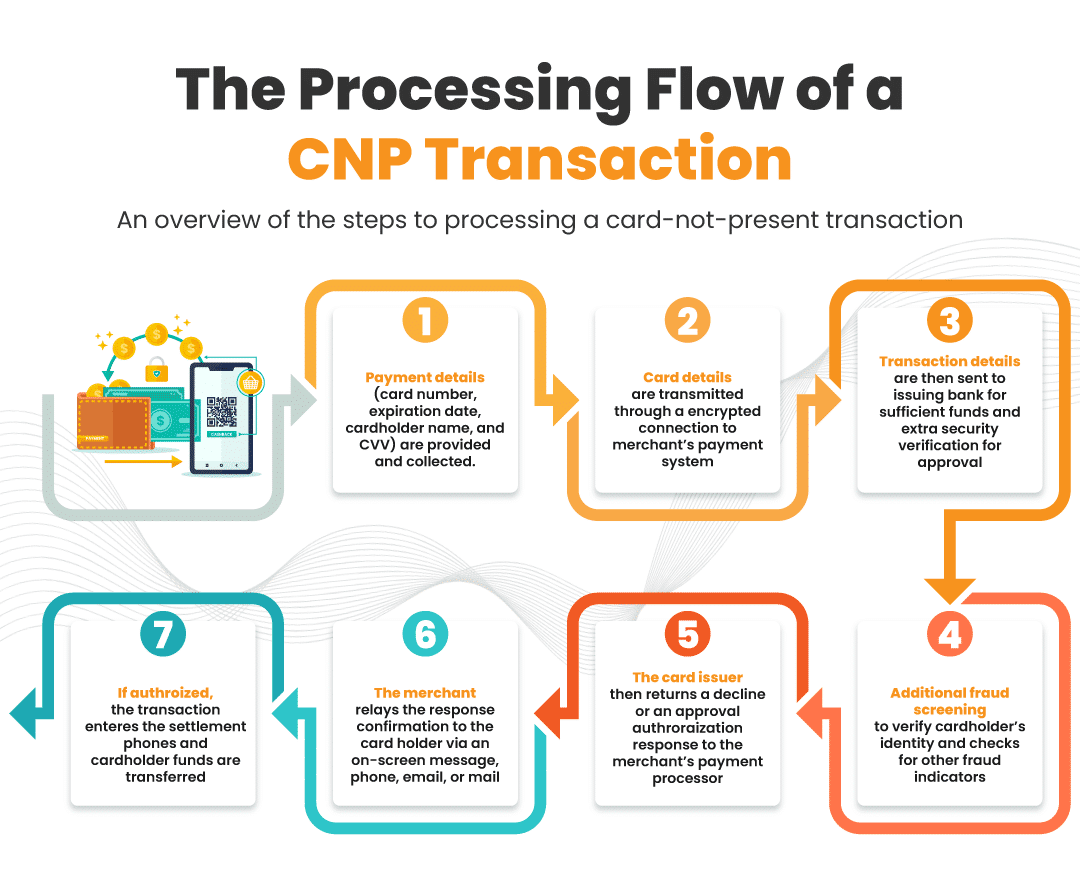
The processing flow of a CNP transaction
Processing a card-not-present transaction involves several key steps. Here’s an overview of these steps:
Step #1 – Collection of payment information: The process begins with the cardholder providing their payment details. This can be done by entering card information on a website, over the phone, or via a mail order form. The essential details typically include the card number, expiration date, cardholder name, and the CVV.
Step #2 – Transmission of card details: Once the card information is collected, it is transmitted to the merchant’s payment system. This is often done in online transactions through a secure, encrypted connection to protect the data from unauthorized access.
Step #3 – Payment authorization: The merchant’s payment gateway or processor sends the transaction details to the card-issuing bank for approval. This step checks the card’s validity, ensures the cardholder has sufficient funds or credit, and verifies other security measures like the CVV and billing address (the account verification mentioned above).
Step #4 – Fraud screening: Many payment processors incorporate additional fraud screening measures. These may include checking the transaction against known fraud indicators, verifying the cardholder’s identity, and employing risk management tools like machine learning algorithms.
Step #5 – Authorization response: The card issuer returns a response to the merchant’s payment processor. This response either approves or declines the transaction. If approved, it includes an authorization code; if declined, a reason is usually provided.
Step #6 – Confirmation to cardholder: The merchant receives the response and relays it to the cardholder. For online transactions, this is typically an on-screen message. This might be communicated via email, phone, or mail for phone or mail orders.
Step #7 – Settlement and funding: Once the transaction is authorized, it enters the settlement phase, where the funds are transferred from the cardholder’s bank to the merchant’s account. This process can take a few days and is usually handled by the merchant’s bank and the payment processor.
Maintaining the security and privacy of the cardholder’s information is paramount throughout these steps. Compliance with standards like Payment Card Industry Data Security Standard (PCI DSS) is critical to protect against data breaches and fraud in CNP transactions.
The role of the payment processor and merchant acquirer
In CNP transactions, the payment processor is the intermediary between the merchant, card networks, and banks. Their primary function is to handle the authorization of transactions. When a customer purchases, the processor receives the transaction details and forwards them to the relevant card network and the customer’s issuing bank. This step involves verifying the transaction’s validity and ensuring the customer has adequate funds or credit.
Additionally, payment processors are responsible for maintaining high security and fraud prevention standards. They employ advanced tools to detect and mitigate fraudulent activity and ensure transaction data is encrypted and secure, adhering to PCI DSS guidelines.
Payment processors
giving you trouble?
We won’t. KORONA POS is not a payment processor. That means we’ll always find the best payment provider for your business’s needs.
The merchant acquirer, or acquiring bank, is another vital player in CNP transactions, providing the necessary infrastructure for merchants to accept card payments. They offer merchant accounts, which are special accounts where the funds from card sales are initially deposited. This role is crucial because it enables businesses to process and receive credit and debit card payments, a core component of eCommerce and remote transactions. Beyond just facilitating these transactions, the acquirer also manages the settlement of funds. They receive payments from the cardholder’s issuing bank and deposit these funds into the merchant’s account, ensuring they receive payment for their sales.
CNP Fraud And Different Types of CNP Fraud
CNP fraud occurs is a type of retail fraud when using stolen credit or debit card information to make unauthorized transactions where the physical card is not required, such as in online purchases, over-the-phone orders, or mail orders.
This type of fraud exploits the lack of physical verification of the card and cardholder, allowing the perpetrator to conduct transactions with just the card number, expiration date, and security code.
Since the fraudster does not need the physical card, CNP fraud is a prevalent issue in digital and remote commerce, posing significant challenges for merchants and consumers in maintaining transaction security.
Stolen card information fraud: This occurs when fraudsters acquire card details through hacking, phishing, or skimming devices and use them for unauthorized online or over-the-phone purchases.
Identity theft: In this scenario, criminals obtain personal information about a cardholder and use it to open new accounts or make transactions in their name, often leading to significant financial loss and credit score damage.
Account takeover: Here, fraudsters gain access to a cardholder’s existing account, usually by obtaining login credentials. They then make unauthorized transactions or change account details to divert goods and funds.
Interception fraud: This involves fraudsters intercepting goods purchased online by modifying the delivery address after placing an order, ensuring the goods are delivered to them instead of the legitimate cardholder.
Chargeback fraud (or friendly fraud): This involves a cardholder disputing a legitimate charge to their card, falsely claiming it was unauthorized, to receive a refund and keep the purchased goods or services.
Triangulation fraud: This sophisticated fraud involves setting up a fake online storefront to collect card details from purchasers, who then receive their goods from a legitimate third-party site that the fraudster has used to place the order using the stolen card details.
Best Practices for Retailers Accepting CNP Transactions
Retailers can identify and prevent Card Not Present (CNP) fraud through several strategies:
Use address verification service (AVS) and CVV Checks: AVS compares the billing address provided by the customer with the one on file with the credit card issuer. Similarly, asking for the CVV adds an extra layer of security.
Use fraud detection tools: Several fraud detection tools can help retailers identify fraudulent transactions. These tools typically use a combination of factors, such as IP geolocation, device fingerprinting, and transaction history, to assess the risk of fraud.
Use a reputable payment processor: Choose a payment processor with a good reputation and strong fraud protection features.
Limit shipping options: Consider limiting shipping options to countries where you typically ship and to addresses that match the billing address.
Use a chargeback prevention service: A credit card chargeback prevention service can help you to identify and dispute fraudulent chargebacks.
Stay on top of blacklists: Consult frequently updated blacklists of known fraudulent addresses, names, IPs, etc., and screen orders against these.
How Much Does it Cost to Process Credit Cards Remotely?
The cost of processing credit cards remotely is typically slightly higher than processing credit cards in person. This is because remote transactions are considered higher risk, as the processor does not have physical possession of the card when the transaction is processed.
On average, merchants can expect to pay around 2.% to 3% in credit card processing fees for remote transactions. This includes the interchange fee, set by the credit card networks, and the processing fee, established by the payment processor. In addition to the interchange and processing fees, merchants may have to pay a monthly fee and/or a per-transaction fee to their payment processor. These fees vary depending on the processor and the merchant’s account type.
Accepting Card-Not-Present Transactions With KORONA POS
KORONA POS is a point of sale system that enables businesses to securely accept card-not-present transactions, allowing customers to pay remotely without physically presenting a card. This is advantageous for businesses selling online or over the phone. With KORONA POS, sensitive customer payment information is tokenized during checkout, meaning card details are replaced with unique tokens that cannot be decrypted. This protects customer data and reduces the risk of fraud.
Furthermore, KORONA POS integrates effortlessly with various payment processors, making it a versatile choice for different business needs. KORONA POS seamlessly integrates in-store and online sales data into one unified platform.
All transactions, whether completed in-person or remotely, are logged in the same system. This gives business owners a holistic view of their operations and sales performance. KORONA POS makes accepting remote payments simple and secure. Book a demo now with one of our product specialists by clicking the button below.
FAQs: Card-Not-Present Transaction
A card-not-present (CNP) transaction occurs when a payment card is not physically presented at the time of the transaction. This is typical in online purchases, telephone orders, or mail orders, where the cardholder provides card details verbally or through a website.
Limits on card-not-present transactions depend on the policies of the card issuer and the merchant. Some issuers may impose lower limits for CNP transactions to reduce fraud risk, while others may not differentiate between CNP and card-present transaction limits.
A card-present transaction happens when the cardholder physically presents the card for payment, such as swiping, inserting, or tapping the card on a point-of-sale terminal. These transactions typically require the cardholder to be physically present to complete the transaction.